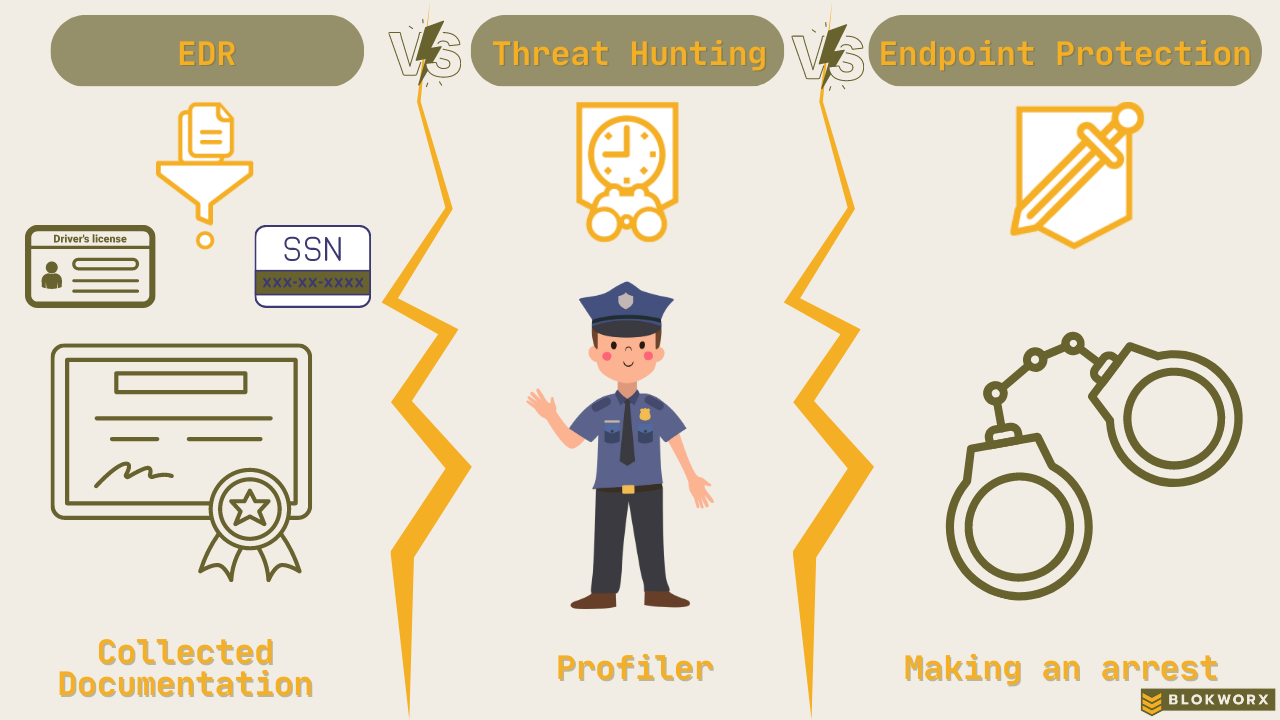
It seems like everyone you speak with has their favorite tool – EDR v. threat hunting v. endpoint protection. Unfortunately, this often leads to relying on one tool while ignoring the others, and other times conflating one tool’s capabilities into another. Realistically, EDR, threat hunting, and endpoint protection are all important for security. Why? Because they are distinctly different and perform very different roles. Let’s see if we can explain this in non-security terms that anyone can understand – preventing and responding to a crime.
Collected Documentation v. EDR
These are the passively collected documents and records regarding a person. Birth certificate, drivers’ license, passport, traffic tickets, Facebook posts, Twitter followers, purchase receipts, etc. When collected for a criminal investigation, they paint a picture of a person, indicating potential motive and likely behavior; but they’re just bits of information, not actionable by themselves.
Similarly, EDR is a mechanism of data collection for the use of a threat analytics engine (XDR, EDR, SIEM/SOAR). They provide endpoint activity data for further analysis to determine the presence of indicators of compromise (IOCs) or malicious activity. At the end of the day, EDR collects data; but cannot act on its own. It can simply be used as a solid data source and telemetry in the event of an issue.
Profiler vs. Threat Hunting
A profiler assists in a criminal investigation by identifying the type of person most likely to have committed a crime based on typical characteristics and behaviors. They illustrate the most likely perpetrator based on known characteristics or corroborating evidence and alert the authorities to guide their search.
Threat Hunting programs look for artifacts of vulnerabilities that can be exploited. They think like a hacker, proactively searching for IOCs and hunting vulnerabilities likely to cause damage based on signatures from a list of known vulnerabilities and exploitations. Then, they alert on these IOCs or vulnerabilities for further actionability. Many appreciate the heads-up style alerts that seemingly predict the future.
Making an Arrest vs. Endpoint Protection
Collected documentation may paint the picture of someone likely to commit a crime, a profiler may indicate the probable perpetrator based on description and illustration, but the police cannot make an arrest until there’s a crime committed. Best case, they can catch the perpetrator in the act, stopping them from causing harm, and leaving little doubt as to the culprit.
Similarly, endpoint protection doesn’t work until there is an active threat. Once endpoint protection detects something amiss, it can stop the bad actor in their tracks, shutting down the execution of malware or preventing a dangerous download, thus remediating the threat. It reactively inhibits the execution of malicious code and/or scripts.
The Power of Three
In short, threat hunting can provide a heads-up alert about a potential danger. Endpoint protection remediates that danger once the threat becomes active. Then, EDR is the data repository that tells the whole tale. Think of these three tools as equally important to a full cybersecurity defense, not a competition between EDR v. threat hunting v. endpoint protection.





